Introduction
Threat hunting has become an essential cybersecurity practice for organizations looking to proactively identify and mitigate threats. As cybercriminals become more sophisticated, organizations must evolve their security measures to effectively detect and respond to potential threats. This article will provide a comprehensive introduction to threat hunting, the techniques and tools involved, and practical examples and use cases.
I. What is Threat Hunting?
Threat hunting is the process of proactively searching for and identifying potential threats in an organization’s network. It goes beyond traditional security measures, such as firewalls and antivirus software, by examining patterns and anomalies that may indicate a cyber attack. Threat hunting aims to detect and mitigate threats before they can cause significant damage to an organization’s assets and reputation.
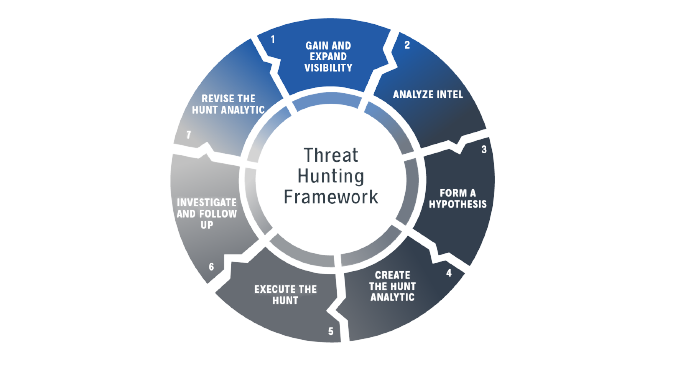
II. Techniques for Threat Hunting
- Hypothesis-driven hunting
This approach involves creating a hypothesis about a potential threat based on intelligence, alerts, or industry trends. The threat hunter then searches for evidence of this threat in the network. For example, a hypothesis could be that an attacker is using a specific type of malware to infiltrate the network.
- Indicator of Compromise (IOC) hunting
IOC hunting focuses on detecting known indicators associated with specific threats, such as IP addresses, domains, file hashes, or malware signatures. By comparing these indicators against network logs and other data sources, threat hunters can identify potential security breaches.
- Machine learning and analytics-driven hunting
This approach leverages machine learning algorithms and data analytics to identify patterns and anomalies that may indicate a threat. By automating the analysis of vast amounts of data, machine learning and analytics-driven hunting can help detect previously unknown threats and reduce false positives.
- Threat intelligence-driven hunting
This technique involves using external threat intelligence feeds, such as reports from security vendors or industry-specific threat-sharing groups, to search for known threats or vulnerabilities in the network.
III. Tools for Threat Hunting
- Security Information and Event Management (SIEM) systems
SIEMs collect, store, and analyze security event logs from various sources in an organization’s network. They can help threat hunters identify suspicious activities, correlate events, and generate alerts.
- Endpoint Detection and Response (EDR) solutions
EDR solutions monitor and collect data from endpoints, such as workstations and servers, providing visibility into potential threats. They can detect suspicious activities, isolate affected systems, and provide remediation options.
- Network Traffic Analysis (NTA) tools
NTA tools analyze network traffic to detect anomalies and potential threats. They can help identify command and control (C2) communications, data exfiltration attempts, and other malicious activities.
- Threat Intelligence Platforms (TIP)
TIPs collect and manage threat intelligence data from various sources, including commercial feeds, open-source intelligence, and industry-specific sharing groups. They can help threat hunters identify relevant threats and IOCs to incorporate into their hunting activities.
IV. Examples and Use Cases
- APT29 (Cozy Bear) attack detection
In this hypothetical scenario, a threat hunter receives intelligence on APT29, a nation-state sponsored group known for its stealthy tactics. They create a hypothesis that the group might be using spear-phishing emails to infiltrate the network. By analyzing email logs and correlating them with known APT29 IOCs, the threat hunter identifies a spear-phishing email and blocks the attack.
- Ransomware attack prevention
In another example, a threat hunter uses machine learning and analytics-driven hunting to analyze network traffic. They identify an unusual spike in outbound traffic, which could indicate a data exfiltration attempt. Upon further investigation, the threat hunter discovers that a ransomware attack is in progress and takes action to contain and remediate the threat.

V. Building a Threat Hunting Team
- Roles and Responsibilities
A successful threat hunting team consists of individuals with diverse skill sets and expertise. Key roles include:
- Threat Hunters: Skilled cybersecurity professionals responsible for conducting proactive searches for threats and analyzing collected data.
- Security Analysts: Individuals who assist threat hunters by monitoring and investigating alerts, analyzing logs, and correlating events.
- Incident Responders: Team members responsible for containing and remediating threats once they are detected.
- Threat Intelligence Analysts: Professionals who collect, analyze, and manage threat intelligence data to inform the threat hunting process.
- Training and Skill Development
Investing in ongoing training and skill development is crucial for an effective threat hunting team. This can include:
- Formal cybersecurity certifications, such as the GIAC Certified Threat Hunter (GCTI) or Certified Cyber Threat Hunting Professional (CCTHP).
- Attending industry conferences, workshops, and webinars to stay up-to-date on the latest threat hunting techniques, tools, and trends.
- Participating in threat hunting exercises, simulations, or Capture the Flag (CTF) events to practice and improve skills.
VI. Measuring Threat Hunting Success
To gauge the effectiveness of your threat hunting program, it’s essential to establish Key Performance Indicators (KPIs) and track progress over time. Some relevant KPIs include:
- Time to Detect (TTD): The time it takes to discover a potential threat from the moment it enters the network.
- Time to Contain (TTC): The time it takes to contain a threat once it has been detected.
- Time to Remediate (TTR): The time it takes to completely remediate a threat and restore affected systems.
- Number of detected threats: A measure of the total number of threats detected by the threat hunting team.
- False positive rate: The percentage of false alarms generated by the threat hunting process.
VII. Conclusion
As cyber threats become more sophisticated, organizations must adopt proactive measures, such as threat hunting, to effectively protect their networks and assets. By understanding the techniques and tools used in threat hunting and building a skilled team, organizations can improve their cybersecurity posture and better respond to emerging threats.
Practical examples and use cases, like the APT29 and ransomware attack scenarios, highlight the importance of threat hunting in detecting and mitigating potential attacks. Continuously monitoring KPIs and investing in training and skill development will ensure the ongoing success of your threat hunting program.
VIII. Integrating Threat Hunting with Other Security Practices
For a comprehensive cybersecurity approach, it is essential to integrate threat hunting with other security practices within your organization. Key areas of integration include:
- Incident response
When threat hunters detect a potential threat, they must work closely with the incident response team to contain and remediate the threat. Integrating threat hunting and incident response can improve the overall efficiency and effectiveness of your security program.
- Vulnerability management
Threat hunting can help identify previously unknown vulnerabilities or misconfigurations in your network. Collaborating with the vulnerability management team can ensure that these issues are addressed promptly, reducing the risk of exploitation.
- Security awareness training
As threat hunters uncover new attack vectors, techniques, and tactics, this information should be incorporated into your organization’s security awareness training programs. Educating employees on the latest threats and how to recognize and report them can help prevent successful attacks.
IX. Case Studies
- Targeted Phishing Campaign
A financial institution was targeted by a sophisticated phishing campaign. The threat hunting team identified the campaign by analyzing email logs for suspicious patterns and correlating them with known phishing IOCs. By working closely with the incident response team, they were able to quickly block the malicious emails and prevent any successful compromises.
- Advanced Persistent Threat (APT) Detection
A large multinational corporation discovered an APT group had infiltrated their network. The threat hunting team used threat intelligence and machine learning-driven hunting techniques to identify the group’s presence. The team worked with the incident response team to contain and remediate the threat, ultimately preventing further data exfiltration and system compromises.
X. Future of Threat Hunting
As cyber threats continue to evolve, so will the discipline of threat hunting. Organizations can expect the following trends to shape the future of threat hunting:
- Increased automation and machine learning
The use of automation and machine learning will continue to grow in the field of threat hunting. As data volumes increase, these technologies will become essential for analyzing and identifying threats more efficiently and effectively.
- Integration with Artificial Intelligence (AI)
AI-powered tools and systems will play a more significant role in threat hunting, helping to identify complex patterns and relationships that might be challenging for human analysts to detect.
- Collaboration and threat sharing
Organizations will increasingly collaborate and share threat intelligence data to improve their threat hunting capabilities. This collaboration will enable more efficient identification and mitigation of emerging threats on a global scale.
- Greater focus on Zero Trust security
As organizations adopt Zero Trust security models, threat hunting will become an integral component of this approach. Threat hunters will need to focus on identifying and mitigating threats within the network, even when traditional perimeter defenses are in place.
XI. Comprehensive Conclusion
Threat hunting has become a vital component of modern cybersecurity programs as organizations strive to stay ahead of increasingly sophisticated cyber threats. By understanding various threat hunting techniques, such as hypothesis-driven hunting, IOC hunting, machine learning and analytics-driven hunting, and threat intelligence-driven hunting, organizations can proactively search for and identify potential threats. Utilizing tools like SIEM, EDR, NTA, and TIP enables threat hunters to perform their tasks more effectively.
Building a skilled threat hunting team, investing in continuous training and skill development, and integrating threat hunting with other security practices, such as incident response, vulnerability management, and security awareness training, are critical to ensuring a comprehensive cybersecurity approach. By monitoring KPIs, such as Time to Detect, Time to Contain, Time to Remediate, and false positive rate, organizations can measure the success of their threat hunting programs and make improvements as needed.
The future of threat hunting will be shaped by increased automation, machine learning, AI integration, collaboration, and threat sharing, as well as a greater focus on Zero Trust security models. By staying informed about these trends and continuously investing in their threat hunting capabilities, organizations can enhance their cybersecurity posture and better protect their assets and reputation.
XII. References
- Giora Engel (2020). Threat Hunting: A Best Practice Guide. Retrieved from https://www.lightcyber.com/whitepapers/threat-hunting-a-best-practice-guide/
- SANS Institute (2017). The Who, What, Where, When, Why and How of Effective Threat Hunting. Retrieved from https://www.sans.org/reading-room/whitepapers/analyst/who-what-where-when-why-effective-threat-hunting-37462
- Sqrrl (2017). Threat Hunting Techniques: Hypothesis Development Workbook. Retrieved from https://www2.deloitte.com/content/dam/Deloitte/us/Documents/risk/us-grc-hypothesis-development-workbook.pdf
- Chris Sanders (2017). Practical Packet Analysis: Using Wireshark to Solve Real-World Network Problems. No Starch Press.

